Vulnerability Management
Protect Your Reputation and Strengthen Your Cybersecurity Program
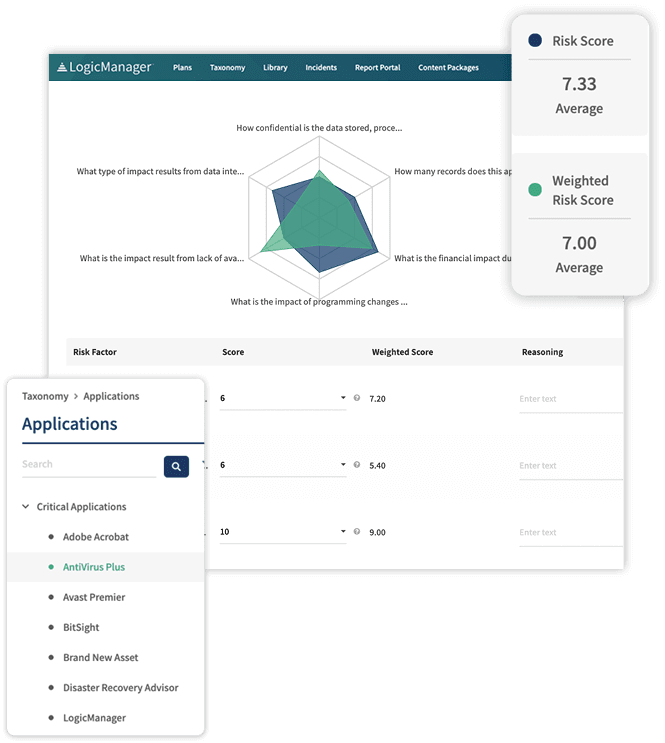
Strengthen your IT Governance program with LogicManager’s comprehensive Vulnerability Management solution. Seamlessly track and manage vulnerability scan results, guiding vulnerabilities to efficient remediation. Harness the power of our dynamic reporting package to gain insights that matter.
- Streamlined Automation: Integrate effortlessly via API to automate vulnerability logging within our ERM platform, enhancing efficiency and reducing manual efforts.
- Tailored Capture: Utilize our customizable, ready-to-use form to capture pertinent vulnerability information, aligning with your unique requirements.
- Automated Workflow: Facilitate stakeholder engagement with automated task initiation based on vulnerability specifics, ensuring timely and effective remediation.
Unlock the potential of our robust reporting engine to pinpoint trends in threat causes and affected areas. Proactively establish enhanced controls and policies, preventing recurrence. LogicManager empowers you to fortify your cybersecurity stance with confidence.

Achieve Vulnerability Management with LogicManager
Streamline your processes
LogicManager includes a variety of ways to automate your tasks, such as workflows, notification scheduling and AI suggestions.
Gain the advantage of ERM
While this package is a point solution, it lives within LogicManager’s fully integrated ERM platform. This means you’ll break down departmental silos and be able to draw key connections across your enterprise.
Maintain a centralized repository
Keep all of your processes and documents in one place. This makes it easier to engage with other employees at your organization and find important information quickly.
Satisfy auditors
With LogicManager, your work is time stamped and performed on a foundation of risk management best practices. This helps you stay prepared for a surprise audit.
What is Vulnerability Management?
Vulnerability management involves identifying, assessing and mitigating risks posed to your organization’s IT security. It also includes remediating issues should any of those risks materialize into an incident. Having a mature vulnerability management program means:
- Proactively examining potential points of exploitation on a computer or network to identify security holes before they are exposed and used as a threat.
- Detecting and classifying system weaknesses in computers, networks and communications equipment and predicting the effectiveness of countermeasures.
- Ensuring timely remediation of vulnerabilities and that patches are actually being applied.
- Reporting on vulnerabilities to identify trends in which applications are the most susceptible, which threats are the most damaging and what controls are functioning.
- LogicManager enables you to execute on these critical processes through automation, best practice standard alignment, cross-departmental engagement and more. Read on to learn about our Vulnerability Management solution package.
Risks
There are a variety of risks associated with an incident involving IT security, including fines and penalties, lawsuits (especially if the vulnerability was known and preventable but nothing was done to mitigate it) reputational damage and ultimately lost customers or investors.
Request a DemoLearn How LogicManager’s Vulnerability Management solution Can Transform Your IT Governance Program
Speak with one of our risk specialists today and discover how you can empower your organization to uphold their reputation, anticipate what’s ahead, and improve business performance through strong governance.


