The Importance of Risk Management in Cybersecurity
Last Updated: March 12, 2024
There’s no two ways about it – in today’s evolving digital world the growing threat of cybersecurity risks is looming over businesses large and small. While the threat to daily operations is certainly one factor that needs to be weighed, businesses also need to be concerned with the reputational risks that can come alongside a cybersecurity incident like a data breach or system hack.
At LogicManger, we know the key to a successful cybersecurity program is inherently tied to an organization’s ability to infuse a risk-based approach and risk management fundamentals into that program. This connection between risk management and cybersecurity will bridge previously existing silos in your organization, bringing forth the information needed to front-line employees and empowering them to effectively manage cyber risks without needing to sink millions of dollars into technology solutions as a band-aid fix.
Why is Cyber Risk Management so Important?
For one thing, data breaches have become more common than ever. As of March, there have been a whopping 5,360+ breaches resulting in more than 30 billion records compromised in 2024. Technology is an inescapable reality of every business. Even the smallest of mom-and-pop shops have an electronic system to conduct credit card transactions, while larger corporations rely on immense data centers to safeguard millions of personal records.With the pervasive integration of technology in business, cyber risk management has crept to the top of many risk managers’ lists. Now that we’ve established why bringing risk management into cybersecurity is so important, we can dive deeper into the specific risks that are posed.
What are the Risks that Come with Cybersecurity?
Reputational Risk
In addition to the more tangible risks we often associate with cybersecurity, such as system downtime or fraud, there is a less tangible category of risk that should be on everyone’s radar: reputation. The era of the See-Through Economy has left businesses with nowhere to hide should any scandals, incidents, or negative news come to fruition. With consumers having access to more information than ever, they cannot only influence the perception of a brand but also the ability to take their business elsewhere if the reputation of a company falls below their expectations. If you still don’t see the importance of reputational risk within the scope of your cybersecurity program, consider the statistics below:
- 60% of consumers hold the companies who collect their data wholly responsible for its protection
- 87% of consumers say they will take their business elsewhere if they don’t believe the company is handling their data responsibly
- 92% of consumers agree that companies must be proactive about data management
As consumers and investors begin to realize just how preventable cybersecurity mishaps are, they’ll turn their business to organizations who have the programs and infrastructure in place to protect them.
Rules and Regulations
Regulators and lawmakers, while not as quick to react to scandal as consumers and investors, remain vigilant. They continue to enhance protections for their citizens’ rights, particularly concerning personal data. As cybersecurity incidents become more frequent, regulatory frameworks are evolving to address these challenges to which businesses must adapt. Today, cybersecurity mishaps can cost a company millions of dollars. The most recent reports estimate the average company will spend $8 million per data breach.
In the United States, President Biden issued an Executive Order in 2024 to protect Americans’ sensitive personal data from exploitation by countries of concern. This marks a significant executive action aimed at safeguarding data security and privacy. At the state level, the landscape is also changing. Over 30 states have introduced or considered security breach notification bills and resolutions. The California Privacy Rights Act (CPRA), enacted in January 2023, amends the California Consumer Privacy Act (CCPA) and introduces new rights such as rectification and data use restriction. Other states like Utah and Connecticut have also passed their own consumer privacy acts, reflecting a growing trend towards more stringent data protection laws.
Globally, the General Data Protection Regulation (GDPR) remains a pivotal change in data privacy, setting a high standard for personal data protection. However, the international data privacy landscape is becoming increasingly complex with countries like China implementing the Personal Information Protection Law (PIPL) and others introducing or updating their own data privacy laws.
The business impact of these developments is profound. Companies must navigate a patchwork of regulations that not only present lofty punitive, financial damages but also require a comprehensive approach to cybersecurity risk management. This includes scoping, prioritizing, tracking, and reporting on critical information across the organization. The average cost of a data breach has escalated, with companies spending significant amounts to mitigate the repercussions.
In this dynamic environment, an integrated approach to cybersecurity risk management is more crucial than ever. It enables organizations to meet broad regulations effectively and maintain resilience against the evolving threats to data security and privacy.
What is a risk-based approach?
A lot of people think the only way to stave off cybersecurity mishaps is by investing millions of dollars in advanced technology like a new network infrastructure. As we’ve demonstrated, cybersecurity is and should be a top priority, but it doesn’t warrant that kind of cash, especially because it’s completely unnecessary without governance processes to ensure it’s used effectively! Technology can fail, patches can be left undeployed, and upgrades can go unscheduled. Taking a risk-based approach to cybersecurity risk management is the only way to ensure your company’s technology doesn’t fall short, the people in your organization are following procedures, and your business is fully protected.
The first step to implementing a risk-based approach is understanding that operating in silos hinders success. IT professionals are often frustrated when executive management tasks them with improving the company’s entire cybersecurity program. This is because the IT department only holds a small piece of the puzzle. Technology impacts every part of a business. Therefore, cybersecurity risk management is a cross-functional practice that IT can’t do alone.
What you’ll uncover after honing in on the cross-functional work is that the risk-based approach does not come with any new work! Most of the information that is needed to implement cybersecurity policies, procedures, and testing already exists within your organization. Utilizing a connected, centralized enterprise risk management platform will bring all of the information you need into one hub while simultaneously removing the need for things like spreadsheets or fragmented offline systems.
Once your team is working off of the same system, they’ll also be able to speak the same risk language. It’s paramount that teams are able to speak in common terms and objectively judge risks off the same scale. This will help to facilitate communication between departments and allow you to ask the right questions on the journey to a stronger program. Consider the table below for a better approach to asking the right questions and ensuring you’re effectively mitigating risk.
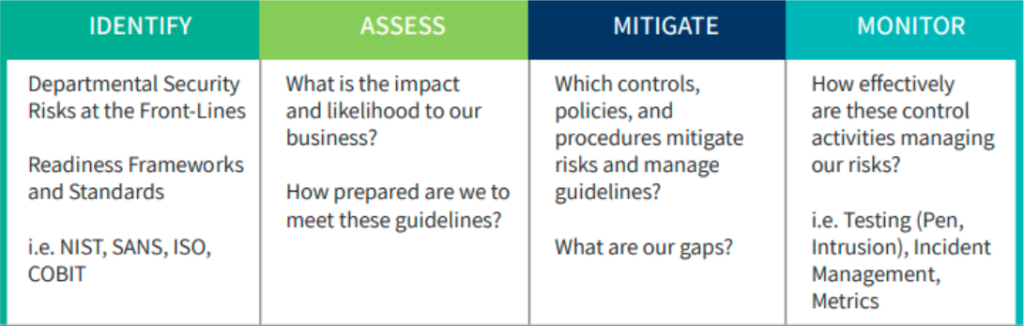
Following this approach to asking the right questions will take you beyond the basics, ‘Are we following the framework?’ and connect the dots to uncover the risks that are actually being addressed and whether or not you’re equipped to handle them.
Now that you have a clear idea of the methodology behind a risk-based approach, you’ll need to engage other departments in identifying, assessing, and mitigating risk, as well as monitoring the effectiveness of your controls.
Download the full guide to uncover real-life scenarios and training exercises your team can adopt on the road to a stronger, more impactful cyber risk management program.
