Privacy Risk Management Program
Unify governance, compliance, and response to safeguard personal data and build trust.
Every interaction, from clicks to transactions, involves personal data, safeguarding privacy is more than a compliance checkbox—it’s a core business responsibility. We understand the pressure privacy leaders face: growing data volumes, evolving regulations, and the need to prove accountability across silos.
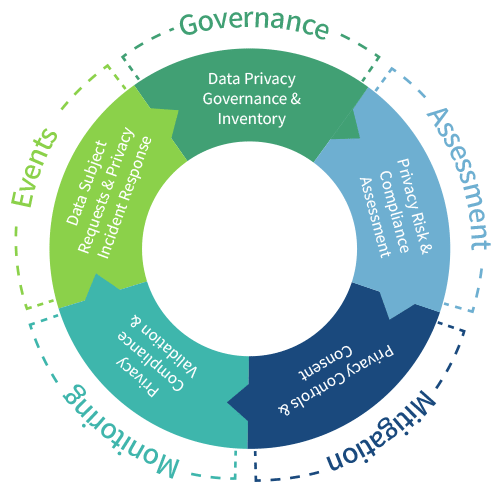
LogicManager’s Privacy Risk Management Program connects your data governance efforts under one roof. It helps you prioritize what matters most, engage the right stakeholders, and stay ready to respond—whether it’s a subject access request, regulatory inquiry, or breach.
Designed for privacy, legal, compliance, and IT teams, the program manages access controls and consent, tracks policies, and ensures consistent practices. With LogicManager as your source of truth, you gain the visibility and confidence needed to govern personal information effectively.
Where Are You in Your Risk Journey?
No matter where you’re starting from, we meet you there—and take you further. Choose the path that sounds most like you and watch how LogicManager transforms your approach to security and governance.
You’re manually updating rows and fighting fires with every audit. Watch how LogicManager helps you replace chaos with clarity—and get back hours in your week.
You’re logging controls and assessments into a passive system with no real follow-through. See how LogicManager turns your governance into performance.
You’re manually updating rows and fighting fires with every audit. Watch how LogicManager helps you replace chaos with clarity—and get back hours in your week.

Engaging Teams, Roles and Responsibilities
Privacy is too important—and too interconnected—to be managed in isolation. That’s why our Privacy Risk Management Program is built for unlimited users with role-based access and clear separation of responsibilities. From Legal and IT to Compliance, Operations, and frontline employees handling sensitive data, every stakeholder has a defined role in the solution.
Each user sees only what they need, takes action within their permissions, and stays aligned through centralized workflows and standardized processes. For example, IT can manage access controls, Legal can respond to subject access requests, and Compliance can monitor adherence to data handling policies—all without stepping on each other’s toes.
The result? A program that’s coordinated, consistent, and defensible
Your Roadmap to Privacy Risk Management Success
Turning Activities Into Actionable Intelligence
Privacy isn’t just about compliance—it’s about trust. LogicManager helps you go beyond documentation by connecting policies, controls, and data responsibilities across your organization.
With Risk Ripple Intelligence, you can instantly trace how a single control failure, subject request, or incident affects downstream processes, systems, and third parties. When something changes—whether it’s a law, a breach, or a DSAR—you’ll already have the visibility and structure to respond quickly and confidently.
Dashboards, insight workbenches, and regulator-ready reports reduce preparation time, strengthen defensibility, and ensure your privacy program stands up to scrutiny.
Security risk management isn’t just about checking boxes—it’s about showing impact. LogicManager transforms your operational efforts into executive-ready intelligence with built-in reporting, customizable insight workbenches, and our proprietary Risk Ripple technology.

Request a LogicManager Demo

Discover how LogicManager’s Privacy Risk Management Program helps you enforce accountability, protect personal data, and prepare for what’s ahead.
Talk to a risk specialist today to reduce response time—and prevent fraud, waste, and negligence across your privacy landscape.