Security Risk Management Program
A holistic, governance-driven approach to managing security risk across your entire enterprise
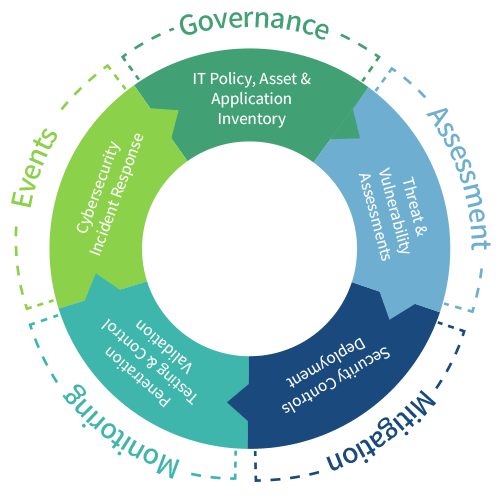
Security is no longer just an IT problem—it’s an enterprise risk. The Security Risk Management Program is your end-to-end framework for proactively identifying, assessing, and mitigating the risks that threaten your business's systems, data, and reputation. Designed for organizations that take governance seriously, this program arms security leaders with the structure and intelligence they need to stop reacting to threats—and start eliminating them before they hit.
This is your path to governance-led security: a single source of truth to define policies, automate testing and validation, align controls to frameworks, and coordinate incident response across all stakeholders. With LogicManager’s Risk Ripple Intelligence, every user, system, and policy is connected—so no threat slips through the cracks.
Where Are You in Your Risk Journey?
No matter where you’re starting from, we meet you there—and take you further. Choose the path that sounds most like you and watch how LogicManager transforms your approach to security and governance.
You’re manually updating rows and fighting fires with every audit. Watch how LogicManager helps you replace chaos with clarity—and get back hours in your week.
You’re logging controls and assessments into a passive system with no real follow-through. See how LogicManager turns your governance into performance.
You’re manually updating rows and fighting fires with every audit. Watch how LogicManager helps you replace chaos with clarity—and get back hours in your week.

Engaging Teams, Roles and Responsibilities
Cybersecurity is too critical—and too cross-functional—to be siloed in one department. That’s why our Security Risk Management Program is built for unlimited users with role-based access and separation of duties baked in. From the CISO setting strategy to the Incident Response Team, IT Risk Oversight, Security Engineers, Governance Committees, and System Admins, every stakeholder has a secure place in the platform.
Each user sees only what they’re responsible for, acts within defined permissions, and stays coordinated through centralized workflows and shared standards. For example, security engineers can configure scans, while governance leaders track remediation without risking system exposure. The result? A program that’s proactive, accountable, and fully defensible—just like your security posture should be.
Your Roadmap to Security Risk Management Success
Turning Activities Into Actionable Intelligence
Security risk management isn’t just about checking boxes—it’s about showing impact. LogicManager transforms your operational efforts into executive-ready intelligence with built-in reporting, customizable insight workbenches, and our proprietary Risk Ripple technology.
Risk Ripple connects the dots across your environment—linking vulnerabilities to assets, controls to policies, and incidents to downstream consequences. That means when something changes, you see its impact across the entire program in real time.
With tailored dashboards and automated reporting, CISOs and leadership teams can demonstrate risk reduction, control effectiveness, and business alignment—all without pulling manual reports or chasing down data. Whether you’re preparing for the board, an auditor, or a governance review, your insights are already there—accurate, defensible, and actionable.
This isn’t just visibility—it’s intelligence that drives performance.

Request a LogicManager Demo

Discover how LogicManager’s Security Risk Management Program empowers you to govern cybersecurity as an enterprise-wide risk—not just an IT issue.
Speak with a risk specialist to see how you can align policies, validate controls, and engage stakeholders in a proactive, defensible approach to security oversight.