SOC 2 Compliance Software
SOC 2 compliance software from LogicManager offers a comprehensive solution that enables your organization to mitigate vendor risk and meet your organization's compliance requirements. Get more peace of mind knowing you're achieving this crucial security benchmark.
For additional value:
What is SOC 2 Compliance?
Service Organization Control (SOC) 2 is an auditing process that ensures your organization’s security providers manage your data in a manner that protects your interests and safeguards your clients’ privacy. Maintaining SOC 2 compliance also helps to fulfill other regulatory requirements by establishing IT best practices across your enterprise.
SOC 2 differs from the Payment Card Industry Data Security Standard (PCI DSS), which has more rigid requirements. SOC 2 reports are unique to each organization, though they comprise five Trust Service Principles:
- Security: The security principle ensures that sufficient physical and electronic controls are in place to protect sensitive data. It also provides evidence of these controls and ensures the implementation of appropriate security management steps to respond to threats.
- Availability: This principle covers the ability to identify negative trends regarding data availability. It applies to any organization that relies on data centers or telecommunications companies or provides services that other entities need to function efficiently.
- Processing integrity: This area of SOC 2 compliance entails the implementation of quality assurance process monitoring to protect the integrity of the company’s transactions. For instance, if a business provides IT services, it must outline its methods for safeguarding customer data.
- Confidentiality: Achieving SOC 2 compliance requires the ability to demonstrate that your organization has the technical and procedural means to honor MSAs, DSAs and other contractual arrangements containing confidentiality clauses.
- Privacy: SOC 2 provides a privacy framework that builds trust with customers and stakeholders.
SOC 2 Compliance Risks
Negligence is 100% avoidable — but once you’re found guilty of it, the fees associated with hiring lawyers, consultants and internal specialists skyrocket quickly. Remaining in compliance with SOC 2 (and having a software that documents your due diligence efforts along the way) helps prevent negligence.
Another risk you’re facing by neglecting SOC 2 compliance is missing out on potential customers; many companies and individuals look to ensure that their service providers are keeping their information safe. They’ll often ask for a SOC 2 compliance report, and if you cannot provide one, they may go elsewhere.
This inadvertence can also turn existing customers away. In addition to the incident and negligent legal liabilities, the loss from customer non-renewals and cancellations is significant: it’s estimated that the total average cost of a data breach is $3.8 million.
Why a Risk-Based Approach to SOC 2 Compliance Is Important
Implementing a risk-based approach gives you increased capabilities for ensuring SOC 2 compliance.

COMPLIMENTARY DOWNLOAD:
SOC 2 Compliance Checklist
SOC 2 Compliance Checklist
Discover how to take a risk-based approach to SOC 2 Compliance with our free PDF download.
Benefits of Achieving SOC 2 Compliance
Implementing SOC 2 security controls offers numerous benefits for your organization:
- Enhanced security assurance: The in-depth nature of this auditing process provides more insight into your security controls.
- Cost savings: Getting SOC 2-certified helps to reduce the likelihood of data and security breaches that can have significant financial consequences.
- Protection from reputational damage: By minimizing your security risk, SOC 2 compliance helps to protect your organization’s brand and reputation.
- Competitive advantage: Becoming SOC 2-compliant demonstrates to potential customers and business partners that you’ve taken appropriate steps to safeguard their data.
- Process improvements: Implementing SOC 2-compliant measures helps you streamline your processes and controls to optimize your cybersecurity efforts.
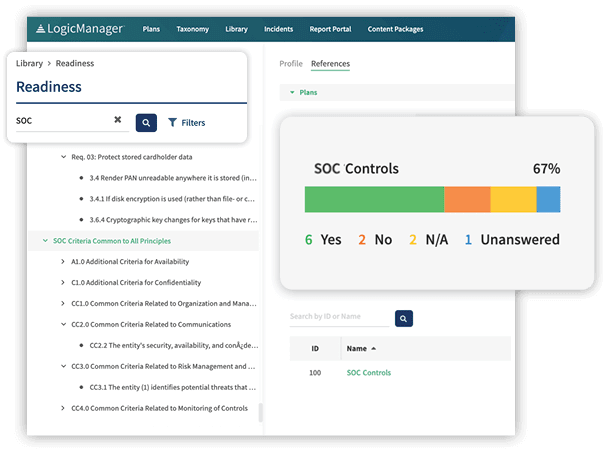
Streamline SOC 2 Compliance With LogicManager
At LogicManager, our risk-based approach to SOC 2 compliance sets us apart from our competitors. We’ll help you create non-siloed compliance programs that add value to your organization and:
- Define responsibilities: Our Readiness Assessment enables you to break your organization’s variety of compliance responsibilities down into defined tasks for assignment to specific departments or individuals. This methodology increases accountability. Our risk assessment tools include best practices to guide you as you establish a solid compliance foundation.
- Facilitate monitoring: The automated testing component of our software allows you to gauge the effectiveness of your compliance program over time via testing and collecting KPIs and other essential metrics. You can also streamline and simplify your audit program.
- Reduce internal labor costs: The One-Click Compliance feature enables you to take a risk-based approach to document analysis. Utilizing advanced artificial intelligence allows you to automap all relevant controls to any compliance plan or risk libraries.
- Ensure timely completion: LogicManager enables you to create personalized home screens that take you directly to your list of compliance-related tasks. It also includes a workflow engine that automatically allocates tasks to the appropriate parties. These features help you keep track of your activities and complete them on schedule.
- Make program improvements: LogicManager’s reporting and dashboard features enable you to visualize past results of your SOC 2s and access testing calendars and other valuable features. Use this information to optimize the results of your compliance initiatives and gain insights that enhance your quest for continuous process improvement.
Related Content
Request a DemoLearn How LogicManager’s SOC 2 Compliance Software Can Transform Your Risk Management Program
Speak with one of our risk specialists today and discover how you can empower your organization to uphold their reputation, anticipate what’s ahead, and improve business performance through strong governance.