What Is Vendor Management? [Complete Guide]
Table of Contents
- Bonus Material: Implementing Risk-Based Third Party Management Guide
- Why Is Vendor Management Important?
- Vendor Risk Management vs. Vendor Management
- 7 Critical Vendor Risk Categories to Monitor
- Building an Effective Vendor Risk Management Framework
- Vendor Management Best Practices
- How to Conduct Effective Vendor Risk Assessments
- Regulatory Requirements for Vendor Risk Management
- Vendor Management Examples and Case Studies
- The Role of Technology in Modern Vendor Risk Management
- How LogicManager Transforms Vendor Risk Management
- Getting Started With Vendor Risk Management
- Build Your Vendor Risk Management Program With LogicManager
Bonus Material: Implementing Risk-Based Third Party Management Guide
Almost every organization relies on an external team to help the business thrive. However, working with vendors is not without risk. In fact, more than 30% of data breaches are the result of third-party breaches, and 54% of surveyed companies reported experiencing a breach due to a third party in 2023. With the adverse consequences of data breaches and other vendor risks, it is more critical now than ever before to develop comprehensive strategies for identifying and mitigating these risks.

Vendor management processes describe how you document information about your third-party vendors, suppliers and business partners. Vendor management tracks who your third parties are, what services they provide, the internal policies that apply to them, and what sensitive information they have access to.
Vendor risk management is a crucial element of your overall management strategy. Vendor risk management involves understanding possible risks and how to reduce the likelihood of challenges arising during your partnership with a vendor. A comprehensive vendor risk management process will evaluate the possible risks of each of your business partners and third-party vendors.
In this guide, you can learn more about what vendor management is and the critical role of vendor risk management in today’s business environment. We discuss the types of risks to monitor, best practices, assessment techniques and other essential information.
Why Is Vendor Management Important?
Vendors have access to valuable information and critical business systems. Maintaining strong relationships and developing a robust risk management strategy is crucial for ensuring the protection of these systems and information.
Comprehensive vendor management helps businesses avoid reputational, financial or operational harm and penalties associated with noncompliance. A risk-based approach to the vendor management process requires you to have a comprehensive understanding of possible risks and how to prepare meaningful remediation strategies to address all threats. This proactive strategy empowers you to better adapt to changing threat landscapes and prevent devastating breaches.
Vendor Risk Management vs. Vendor Management
Vendor risk management (VRM) is a subset of vendor management, and effective vendor management will include a strong VRM program. It is also important to note that VRM differs from third-party risk management, which involves all third parties an organization interacts with, not only suppliers and vendors.
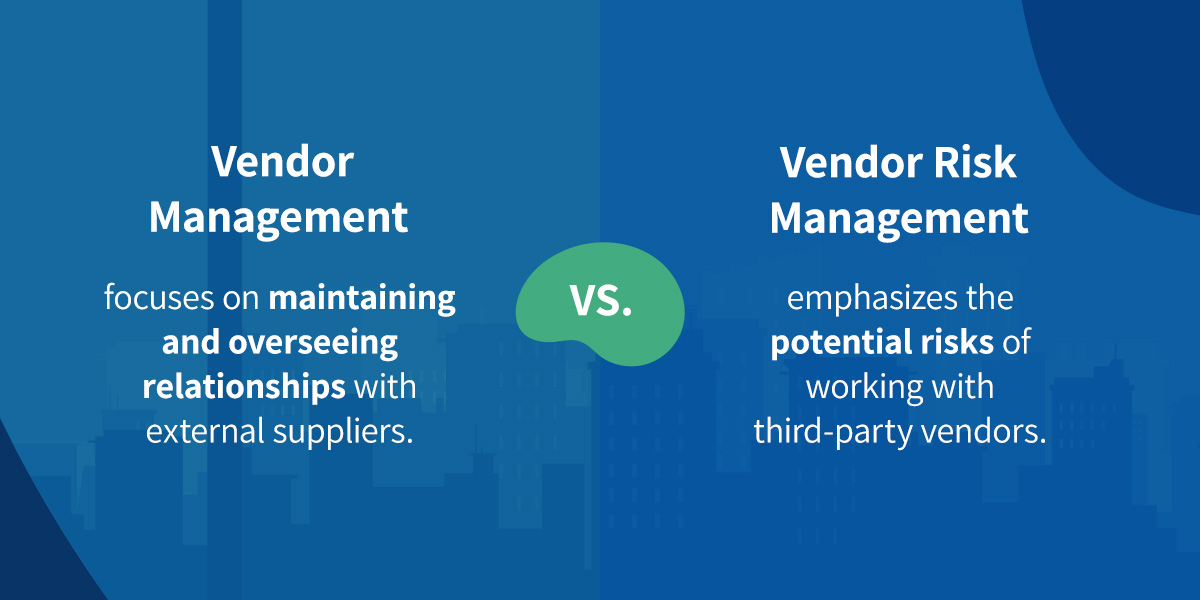
Vendor management focuses on maintaining and overseeing relationships with external suppliers. Alternatively, VRM emphasizes the potential risks of working with third-party vendors. Although these management types often go hand in hand, they vary in:
- Scope: Overall vendor management encompasses all aspects of your relationships, from your initial interaction to contract termination. This broad scope covers the entire vendor life cycle and is cross-functional. Efficient and comprehensive vendor management relies on several departments, including IT, finance, operations and procurement. VRM has a much smaller scope, focusing on potential threats and vendor vulnerabilities.
- Objectives: The primary goal of vendor management is to maximize value within vendor relationships. For example, teams will determine ways to save on costs and improve service levels. Alternatively, VRM aims to minimize vendor-related risks in domains like cybersecurity, finance and operational inefficiencies.
- Processes: Vendor management processes may include activities like vendor selection and onboarding, performance monitoring, relationship building, vendor cost management, and compliance with contractual obligations. VRM will often focus on ongoing risk profile management, incident response planning and vendor security evaluation.
Implementing vendor risk management is crucial for your business’s success, efficiency and reputation. Implementing a strong VRM framework can also help to improve your vendor relationships. By identifying potential risks, ensuring compliance and streamlining efficient processes, you can create a stronger vendor relationship that benefits your organization and your third-party teams.
7 Critical Vendor Risk Categories to Monitor
The first aspect of vendor risk management to understand is the types of risks vendors can pose to your business. There are seven key risk categories you should be aware of when evaluating vendors.
1. Cybersecurity and Data Privacy Risks
Cybersecurity is a growing concern across all industries. With cyber attacks becoming stronger and occurring more quickly, monitoring cybersecurity is more crucial now than ever before. Businesses must identify organizational risk thresholds before quantifying vendor risks. Defining these levels will allow you to easily assess vendor performance and make adjustments where necessary.
As you evaluate vendor performance, delegate special attention to compromised systems within your networks. System breaches can provide crucial insight into how your partners identify and contain attacks to prevent data losses. It is also important to understand the severity, nature and frequency of compromises to craft comprehensive responses.
Cybersecurity regulations are under constant evaluation, and threats are evolving rapidly. You must regularly update your criteria to align with changing cyber landscapes and compliance needs. Ongoing assessment is vital for creating a resilient cybersecurity environment and managing vendor risks as quickly as possible.
2. Operational Risks
When you rely on a vendor for business operations, you run the risk of facing downtime or inefficiencies should something go wrong. If your vendor shuts down or is otherwise unable to deliver promised services, your team may be incapable of performing daily activities. For example, a healthcare clinic that relies on a single supplier for medical device manufacturing or delivery could experience serious consequences should that vendor suddenly cease operations.
It is crucial to create plans for ensuring business continuity amid vendor operational risks. Teams should prepare strategies for offering alternative services and communicating with consumers quickly. Identify your key vendors and quantify the potential impact of any failures. Understanding these risks aids in mitigating challenges and ensuring business effectiveness.
3. Financial and Business Viability Risks
Each vendor can pose financial risks to your organization through lost revenue or excessive costs. Excessive costs can directly impact your financial health, often by increasing operational costs or reducing profitability. Whether a vendor has inefficient shipping routes or has much higher costs than competitors, your business could quickly face excess debt and hindered growth.
It is also crucial to understand a vendor’s financial history and historical performance to determine whether a team is viable for your business. You can conduct credit monitoring and ask for references from organizations with a previous or current relationship with your proposed vendor.
It can be beneficial to leverage a system for tracking sales activity and related tasks associated with your vendors. Vendor risk management platforms can help you regularly assess financial risk and monitor your vendors’ performance reliability. You can also use your historical data to create contingency plans for disruption mitigation or inform new vendor agreements if necessary.
4. Compliance and Regulatory Risks
Your organization likely has unique internal processes and external standards and laws you must adhere to when conducting business. Regulations vary by industry and sector, but adhering to them is essential for avoiding legal penalties and promoting a reliable business reputation. Additionally, there are several types of compliance.
For example, healthcare organizations generally must adhere to strict regulations surrounding sensitive personal information, while financial institutions must follow stringent requirements regarding credit and debit card transactions. If a vendor breach results in the loss of data, such as personally identifiable information, your business will be legally responsible.
Organizations must understand their industry requirements and ensure all vendors meet compliance requirements. Teams must regularly review regulation changes and adjust operations to reduce compliance risks.
5. Reputational Risks
A unique risk when working with third-party vendors is potential reputational damage. Your suppliers and partners are a reflection of your business, no matter how far removed they may seem from your operations. Your vendor’s actions can directly impact customer trust and public brand image, opening the door for decreased sales and overall business value declines when something goes wrong.
During the procurement process, research vendor reputations and look for negative signs like lawsuits and slow responses. Determine how these factors could impact the vendor’s performance and ability to meet your operational demands. Consider every aspect that could impact your brand’s image, from data breaches to unethical material sourcing to service disruptions.
6. Geographic and Geopolitical Risks
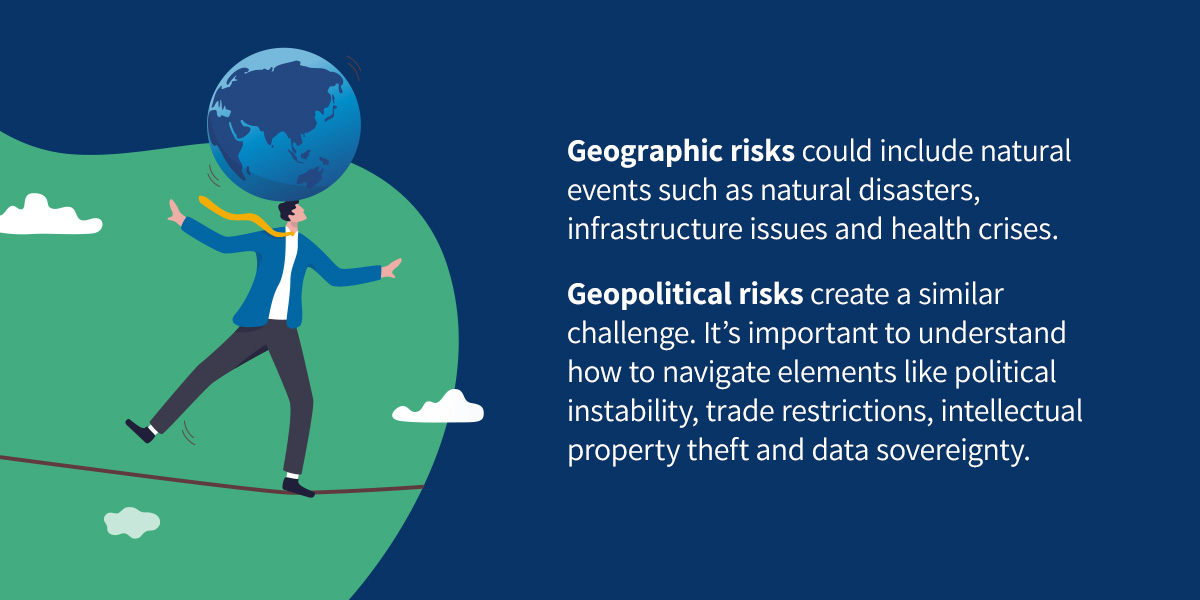
Another challenge to consider is vendor geographic and geopolitical risks. Geographic risks could include natural events such as natural disasters, infrastructure issues and health crises. While these risks can be difficult to determine, there are often some key considerations.
For example, a vendor in Florida is much more likely to experience devastating impacts from hurricanes than one in Virginia. While you may have geographic limitations on the vendors you can choose, there are other ways to navigate these challenges. For example, if you must operate with vendors in Florida, you may have multiple backup options during hurricane season to reduce operational risks and supply chain disruptions.
Geopolitical risks create a similar challenge. If you’re partnering with vendors internationally, it’s important to understand how to navigate elements like political instability, trade restrictions, intellectual property theft and data sovereignty.
7. Fourth Party and Supply Chain Risks
Fourth-party and supply chain risks refer to risks that can arise from your vendors’ vendors. A fourth-party vendor can directly impact your business operations if they fail to meet service requirements with your third-party vendor.
Some common examples of fourth-party vendors include software providers, data centers, cloud service providers and payment processors. Alternatively, supply chain risks present different challenges. For example, you could face problems related to unethical material sourcing, counterfeit goods or raw material shortages.
Before creating a vendor agreement, you must understand each vendor’s network and how it could impact your business. Monitoring continuously and enforcing contractual requirements can help you mitigate these risks. Additionally, strengthening communication with your vendors can help identify ways to improve supply chain resilience and security.
Building an Effective Vendor Risk Management Framework
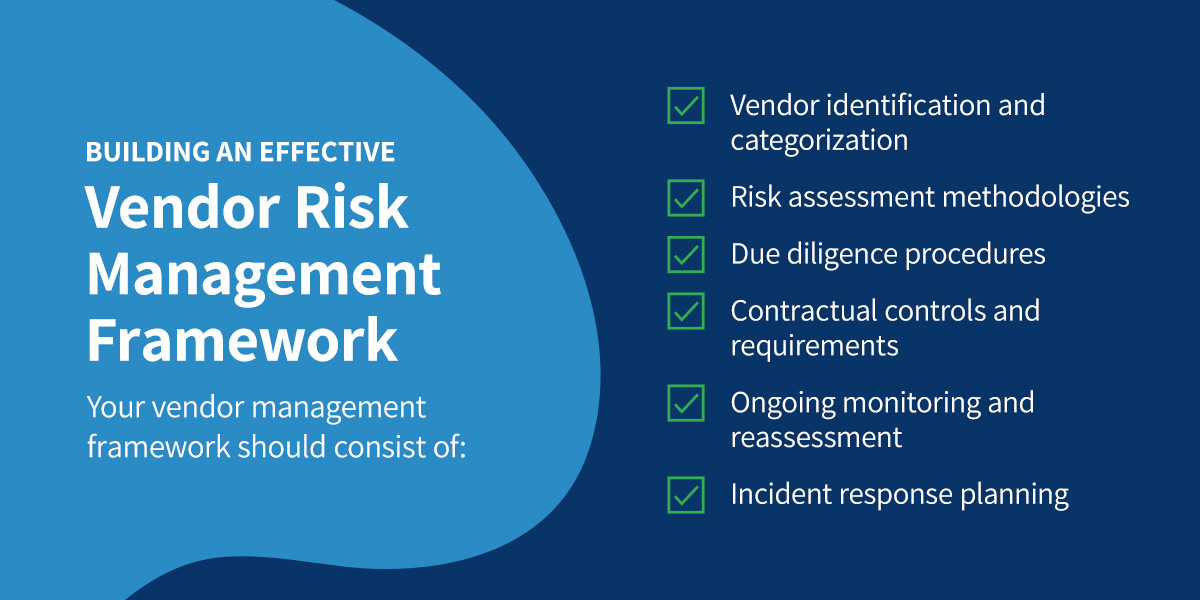
A comprehensive risk management framework helps your business identify, assess and mitigate vendor risks. Your vendor management framework should consist of:
- Vendor identification and categorization: This first stage will create the foundation for your following risk management activities. Identify and categorize your existing vendors. A vendor-managed inventory example could include high-risk, medium-risk, low-risk and no-risk vendors. Be sure to categorize every vendor, even small businesses with low business engagement.
- Risk assessment methodologies: Your next step is to establish risk assessment methodologies. These metrics will guide your vendor risk evaluation. Identify all possible risks, assess the likelihood of each risk occurring and determine the possible impact each risk could have on your business.
- Due diligence procedures: You must conduct thorough due diligence before onboarding potential vendors. Review all relevant compliance certifications, assess operational resilience, evaluate financial stability and determine the effectiveness of cybersecurity measures.
- Contractual controls and requirements: Robust contracts can help reduce the likelihood of vendor-related risks. Be specific in all contractual language and include key clauses to ensure data protection, confidentiality, security and compliance. Include exit strategies in case the vendor becomes non-compliant.
- Ongoing monitoring and reassessment: Effective risk management requires continuous monitoring. Conduct regular compliance reviews and audits. Track vendor performance and use risk assessment tools for real-time insights.
- Incident response planning: Unfortunately, problems can arise despite your best mitigation attempts. Contingency plans are necessary to address security incidents or service failures should they occur. Establish incident response protocols, create business continuity plans and outline communication strategies to inform stakeholders.
Vendor Management Best Practices
One of the easiest ways to understand best practices for vendor risk management is by looking at examples of vendor risk management failure. Take, for instance, the J.M. Smucker Company scandal in February 2018. The FDA announced that low levels of an animal euthanasia drug were detected in canned dog food produced by Smucker’s. Their stock subsequently dropped by 3%, resulting in a loss of more than $400 million in market value.
After the fact, the company stated that they’d identified the root cause of the poisoning to be one supplier and a single ingredient used at one manufacturing facility. Had Smucker’s taken a root cause approach to their vendor risk management process, they would have started by administering risk assessments to key vendors, and risks at those facilities would have been uncovered, prioritized, and mitigated.
Performing a risk assessment helps to identify the true root cause. Your risk assessment can then serve as a roadmap as you design an efficient workflow to make sure that, ultimately, you are protecting your business’s best interests.
Aside from starting off by performing a risk assessment, here are some best practices for taking a risk-based approach to preexisting and new vendor relations:
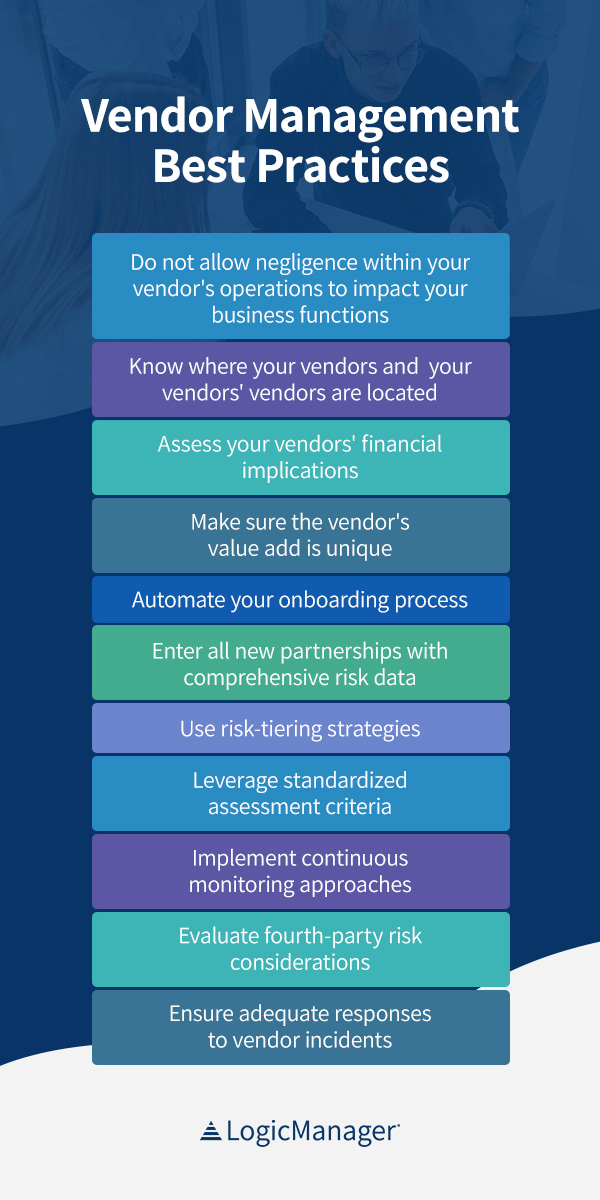
- Do not allow negligence within your vendor’s operations to impact your business functions: Make sure your critical vendors are managing the safety of their own employees as you are managing the safety of yours.
- Know where your vendors and your vendors’ vendors are located: This will keep you tuned into external factors that may be affecting their geographic area at any given time.
- Assess your vendors’ financial implications: Are your vendors contributing to a positive ROI? Taking note of this will help you keep track of which relationships are most valuable to renew.
- Make sure the vendor’s value add is unique: Setting this standard helps you keep unnecessary business expenses to a minimum.
- Automate your onboarding process: Create a reusable but customizable vendor request profile for external contacts to submit. Use this form as a means to add any complex questions that may impact your vendor decision-making.
- Enter all new partnerships with comprehensive risk data: Ask the hard-hitting questions early on — the wellness of your business depends on it.
- Use risk-tiering strategies: Use a vendor risk rating system to determine low-, medium- and high-risk tiers. Manage your relationships by leveraging these ratings and asking high-risk vendors for more frequent reviews.
- Leverage standardized assessment criteria: Ensure your frameworks are consistent and predefined so you hold all vendors to the same standards.
- Implement continuous monitoring approaches: Monitor vendor performance and assess risk regularly. Make adjustments as necessary to remain compliant and secure.
- Evaluate fourth-party risk considerations: Ask your vendors about the criticality of their own vendor relationships. Tier fourth parties by evaluating their impact on your organization.
- Ensure adequate responses to vendor incidents: Craft comprehensive incident responses to ensure business continuity, minimize data losses and inform all relevant parties of the incident.
How to Conduct Effective Vendor Risk Assessments
Vendor risk mitigation strategies begin with assessment techniques. Some beneficial assessment methodologies include:
1. Questionnaires and Surveys
A structured assessment document can help you evaluate vendor risks and quickly identify potential vulnerabilities. Questionnaires and surveys can give an in-depth view of compliance, privacy and security controls so you can determine whether a vendor is worth partnering with. Consider questions like:
- Have you defined and published information security policies?
- Do you have an asset management program to define how to dispose of, handle, classify and inventory assets?
- Does your organization review suppliers who deliver information services, components and systems?
- What are your operations procedures for change management, data backups and patching?
- How do you detect, monitor, plan for and respond to potential threats?
- Can you describe your organization’s incident management process?
- What physical security measures do you employ to ensure on-site security?
- How often do you conduct audits and risk assessments, and what does that process look like?
- What is your approach to disaster recovery and business continuity?
- How does your team approach systems development while maintaining security?
2. Document Review Processes
Document review processes can help you determine whether a vendor is meeting industry standards and regulatory compliance. Incomplete or inconsistent information can help you identify gaps in risk management processes and areas for improvement.
Look for inconsistencies between documented policies and on-site practices. Determine areas where additional monitoring is necessary and whether the vendor has addressed historical challenges and practices continuous improvement.
3. On-Site Assessments
Conducting assessments on-site can reveal weaknesses in risk management that may not be apparent in self-reported vendor data. For example, a vendor may claim they implement physical security measures, but on-site assessments depict inadequate staff training, leading to physical security inconsistencies or vulnerabilities.
You can also use on-site assessments to evaluate operational risk potential. These assessments can allow you to understand a vendor’s operational capabilities and their ability to manage incidents, handle disruptions and ensure business continuity. Assessing these capabilities is especially important when choosing critical service or systems vendors.
4. Automated Scanning Tools
Automation can streamline workflows, including risk management tasks. Vulnerability scanning can empower you to quickly identify vendor application and system vulnerabilities, allowing you to address potential problems before a malicious third party can exploit them.
Automated scanning tools can also enable continuous monitoring and provide real-time alerts regarding threats and new vulnerabilities. These tools can help you prioritize risks and address threats quickly to minimize impact.
5. Industry Certifications
Certifications can reduce the time and effort necessary to ensure due diligence. Partnering with certified vendors can offer peace of mind and make it easier to determine vendor compatibility with your organization.
Industry certifications often require organizations to meet stringent requirements and exhibit ongoing adaptation to meet changing demands. Certifications can serve as evidence of a vendor’s commitment to their industry and highlight their ability to manage risks effectively.
Regulatory Requirements for Vendor Risk Management
Your partners should meet regulatory requirements. Some of the top key regulations and regulators affecting VRM include:
- General Data Protection Regulation (GDPR): The GDPR requires organizations in the European Union to process personal data fairly, lawfully and in a transparent manner. These requirements also apply to third-party vendors. Meeting GDPR compliance requires organizations to implement security measures, obtain information processing consent, store data for the appropriate times and erase personal information at an individual’s request.
- Health Insurance Portability and Accountability Act (HIPAA): Covered entities must ensure all vendors handle protected health information in compliance with HIPAA standards. HIPAA outlines risk analysis requirements, which include identifying electronic personal health information, evaluating external sources of this information, and recognizing the environmental, natural and human threats that could impact systems containing this information.
- Office of the Comptroller of the Currency (OCC): The OCC is the primary bank regulator for covered national entities and federal savings associations. Covered entities must outline their risk management life cycle and clarify that each third-party relationship presents varying levels of risk or criticality to a bank’s operations.
- Federal Trade Commission (FTC): The FTC aims to protect consumers. The Safeguards Rule requires covered entities to ensure customer confidentiality, information security and threat protection. The rule also outlines the need to evaluate third-party app security if an entity uses a vendor to transmit, store or access customer information.
Vendor Management Examples and Case Studies
To truly understand the impact of vendor management, it is beneficial to look at vendor management case studies from well-known companies.
Target
In 2013, Target fell victim to a massive cyber attack. The company had partnered with a third-party refrigeration vendor. A cyber attacker sent a phishing email to this vendor, and after obtaining login credentials for the vendor’s online portal, the attacker was able to gain access to Target’s network.
The result was 70 million customers facing stolen personally identifiable information and 40 million customers dealing with stolen credit card information. This breach alone cost Target over $162 million. In 2017, Target paid $18.5 million in settlements related to the breach, highlighting that poor vendor risk management can have long-lasting consequences. A significant contributor to the breach was Target’s lack of focus on infrastructure vulnerabilities.
Chipotle
Chipotle is another well-known company that felt the impact of poor risk management. The business advertised healthy, fresh, locally-sourced food, and came under fire when they failed to ensure their vendors supported this mission.
In 2015, customers became sick from salmonella and E. coli at several Chipotle locations. Not only did Chipotle face serious reputational damage as a result, but share prices fell, sales plummeted and Chipotle paid a criminal fine that totaled over $25 million.
Since this outbreak event, Chipotle has implemented advanced technologies to improve traceability and inventory management and takes additional measures, such as conducting regular third-party audits, to ensure food safety.
Microsoft
Alternatively, there are great examples of organizations that have prevented vendor-related issues. For example, Microsoft implemented its Supplier Security and Privacy Assurance program to support customer data protection.
This program ensures Microsoft’s suppliers adhere to the unique privacy and security principles at Microsoft. Vendors must implement Microsoft’s privacy controls before beginning a partnership with the organization, and high-risk vendors must also provide independent compliance verification.
J.P. Morgan
J.P. Morgan offers another successful example. The financial institution faced a significant breach in 2014, but has since implemented stronger vetting processes and continuous monitoring to ensure ongoing security. The corporation has also redefined compliance processes and invested in fraud prevention solutions to mitigate risks.
The Role of Technology in Modern Vendor Risk Management
Today, advanced technologies bring immense capabilities and increased benefits to organizations looking to implement vendor risk management. The right technologies can reduce the likelihood of human error, streamline workflows by eliminating repetitive tasks and improve data visibility. You can also enhance collaboration through digital document sharing and access real-time insights for informed decision-making.
You can experience these benefits by leveraging tools and technologies like:
- Risk management platforms: Risk management platforms streamline the processes surrounding risk mitigation. These platforms can adapt to industry regulations, enterprise size, security maturity and vendor ecosystem complexity. These platforms often provide real-time alerts, enable document collection, guide onboarding and offboarding, enhance collaboration with vendors, and ensure advanced reporting and analytics.
- Continuous monitoring tools: Continuous monitoring is crucial for ensuring the constant identification of new threats and quick adaptation to mitigate risks. Many risk management platforms offer continuous monitoring capabilities, but you can also look for additional tools to strengthen your approach. Regardless of the specific monitoring tool you choose, be sure to select one with real-time alerts. Comprehensive monitoring tools will notify you of unusual activity, like credential theft attempts, unauthorized system access and vulnerability exploits.
- Integrated enterprise risk management (ERM) systems: ERM systems leveraging a risk-based approach can improve business performance and enhance peace of mind. These systems can grant overall organizational visibility, allowing teams to shape risks across departments. ERM solutions lead risk identification across the enterprise, assess risk severity based on predefined criteria and connect risk mitigation activities for comprehensive coverage. Additional features like continuous monitoring enhance security efficiency, and reporting empowers you to make data-driven decisions for lasting change.
- Contract management solutions: Contract management solutions incorporate your risk management features and processes to assess and mitigate risks throughout vendor lifecycles. These solutions can prompt contract review, risk assessments and performance monitoring to ensure vendors meet contractual and compliance requirements.
- Artificial intelligence (AI) and automation capabilities: AI and automation can streamline your risk management processes while improving accuracy. With features like real-time insights and trend analysis, these tools can help organizations make informed decisions and get ahead of challenges before they arise. There are numerous ways to incorporate AI and automation, from streamlining vendor onboarding to enhancing contract management to automating compliance checks.
How LogicManager Transforms Vendor Risk Management
With LogicManager, you gain access to a central vendor management hub that supports your business with tailored solutions. LogicManager leverages a unique risk taxonomy approach to organize and categorize vendors and associated risks. Our solution also links insights from across departments to uncover potential threats and recommend actions to address them.
LogicManager makes it easy to implement a comprehensive solution by providing a no-code approach to connect our solution with your existing systems and applications. Your IT team can skip configurations while integrating with more than 500 applications, including Office 365, Slack, Adobe, AWS, HubSpot, Microsoft Teams and more.
You can also use our pre-built templates and content for streamlined workflows. Use our defined risk assessment template, facilitate initiatives with performance ERM management and ensure effective resource use with allocation best practices. We also offer advisory support so you can gain confidence while implementing our solution. Our advisory team can provide insights into business continuity, vendor spend management, dashboard reporting and more to ensure you get the most out of your investment.
To learn more, see what our customers have to say about our capabilities. Our customers have gained full transparency, reduced risks and cut resource usage during risk management processes. We have helped organizations increase efficiency, ensure compliance and prevent negligence.
Getting Started With Vendor Risk Management
If you are preparing to embrace a risk management program, it can be helpful to know what to expect from the process. Actionable steps for implementation include:
1. Preparing for Initial Program Setup
Begin implementation by defining the scope of your VRM program. Establish what types of risk you will be addressing and the vendors you will include. Establish the specific and measurable objectives you wish to achieve. Develop your policy and framework, outlining the tools, procedures and processes necessary to implement your policies. Centralize your vendor information and establish an effective storage and management system for all vendor-related information.
2. Taking Immediate Action
There are several immediate actions you will need to take, including implementing basic security controls and addressing high-risk vendors promptly. Ensure each vendor follows and uses robust security measures like regular updates and multi-factor authentication. Conduct rapid risk assessments for high-risk vendors to identify critical vulnerabilities. Address every known vulnerability and develop an incident response plan, and review existing contracts and renegotiate as necessary to ensure stronger security adherence.
3. Planning Resource Allocation
It is important to allocate a sufficient budget to support your VRM program. You must consider staffing needs, new technologies, training opportunities and other ways to ensure continuous program improvement. Dedicating the right amount of resources to your program can help ensure you follow best practices and robust strategies to meet changing demands.
4. Embracing Maturity Model Progression
With the evolving severity and complexity of threats across physical and virtual landscapes, you will need to progress your VRM program to higher levels of maturity when possible. Enhancing risk monitoring, strengthening collaboration and implementing regular reviews will support higher maturity levels.
Build Your Vendor Risk Management Program With LogicManager
Assessing and mitigating your vendor risks is crucial. While it is impossible to anticipate every possible threat that can occur, leveraging the right technologies and features can mitigate consequences and support your vision for growth and success.
When you need a comprehensive solution for managing contracts, assessing risk, accessing real-time alerts and enhancing peace of mind, trust LogicManager to help. Our powerful risk management software enables you to centralize your efforts while streamlining processes. We’ve been helping customers navigate obstacles and expect the unexpected since 2006.
To experience the LogicManage difference, request a demo today.
You May Also Like: What Should Be Included In A Vendor Contract
Free Download:
How to Implement Risk-Based Third-Party Management
Learn what vendor management risk failures look like and 7 steps to manage this process.