How to Audit Cyber Risk
Steven Minsky

The volume and complexity of the data companies collect is increasing exponentially, which creates major challenges for audit professionals.
When we surveyed hundreds of risk professionals, a staggering 72% considered their company to be most vulnerable in cybersecurity. So, it’s no surprise that auditors are frustrated evaluating the effectiveness of cybersecurity programs across industries when their mandate is entirely about assurance.
However, assurance in-and-of-itself is no small task. Given the sheer volume of data companies are collecting every day, it’s almost impossible for auditors to get their hands around all of the information they need from across their organizations – let alone make sense of that data. How can auditors verify their organizations are protected by internal controls when they can’t make sense of such disparate data?
On October 23 of 2018, I was honored to have been invited to speak at the 2018 All Star Conference hosted by The Institute of Internal Auditors in Las Vegas. In my presentation, I discussed how auditors can succeed in cybersecurity. Effective cybersecurity simply doesn’t require massive technology investments, and all cyber-attacks are preventable.
Of course, a robust cybersecurity program should incorporate technology, but that technology will only properly function with good governance and a proactive mindset at all levels and departments. Technology can fail, patches can be left undeployed, upgrades can go unscheduled. This is where the auditors come in.
Operationalizing a risk-based approach to cybersecurity audits is the only way to ensure processes and policies are being followed. Doing so helps ensure that your company’s technology doesn’t fall short, the people in your organization are following procedures, and your business is fully protected.
Cybersecurity will only get more complex over time.
Corporations are accumulating ever-growing volumes of data. International Data Corporation (IDC) projects a ten-fold increase in global data by 2025. Governments, other companies, consumers, and investors trust this data is kept secure. When a breach happens, this trust is broken and the organization’s reputation is damaged, often irreparably.
Furthermore, as regulators and lawmakers play catch-up, they may feel as if they need to overcorrect, meaning fines and penalties could get even more severe.
A #risk-based process to managing #CyberRisk is the best approach to mobilize employees across all departments and silos; from front-line employees, to process owners, all the way to the board of directors.
Click to tweet! 
To make matters worse, cyber threats will only get more complex as time goes on. Not only is the volume of data that corporations are collecting increasing exponentially; data is being collected in disparate formats from all departments. This makes auditing even more difficult because they need to connect information coming from every function, as different process owners from different departments all hold different pieces of information on cyber risks and controls.
How to Adopt a Risk-Based Approach
Cybersecurity is not and cannot be the sole responsibility of the security or IT teams alone; rather, it requires an all-of-organization approach. For auditors, a risk-based approach to auditing cybersecurity ensures their findings are presented so they can be acted upon by process owners, rather than isolated in a single silo. The first step to implementing a risk-based approach is understanding that operating in silos hinders success.
Data security needs to look at the interdependencies between departments: IT Security, Legal & Compliance, Human Resources, Vendor Management, Environmental, Health & Safety (EHS), Business Continuity & Disaster Recovery (BC/DR), Finance, Audit Management, Risk Management, and more. Auditors need to ensure the controls used in all areas of the business are operating as intended while understanding the insights and accountabilities of different roles relative to cybersecurity.
For example, here’s a high-level look at the insight each group has into cybersecurity elements, and what they’re accountable for:
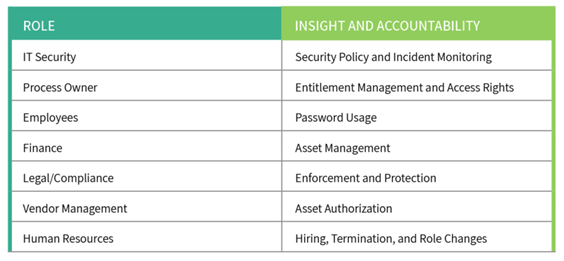
Cyber threats impact every part of a business. Thus, it’s necessary to empower employees across all business areas to identify and report cybersecurity risks. Audit professionals need to be communicating in a way that members of all departments, at all levels, can understand.
Download our free Guide to Improving Your Cybersecurity Program
Download our free guide to learn how a risk-based approach can improve your company’s cybersecurity program.
A risk-based approach is designed to deal with the ever-growing volume of data, as well. While the amount of data is only going to increase over time, it can be standardized and prioritized. A risk-based approach manages this growing complexity by:
- Establishing a common language
- Ensuring the common standardization of processes
- Optimizing the engagement of process owners
- Establishing objective priorities and frameworks
Translate Risk Languages across Departments
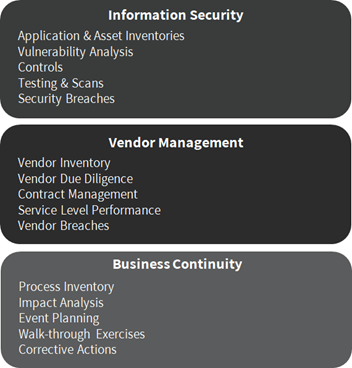
In a traditional, siloed approach, each department treats risks independent from one another. There is no common language or framework to look at an organization’s cyber risk exposure holistically. To illustrate a traditional, siloed approach, a visualization is below.
With a risk-based approach, a common language is established. Different groups use different words to describe the same things, but all activities that relate to cybersecurity can be categorized as either “governance,” “assess,” “mitigate,” “monitor,” or “events.”
A Risk-Based Approach to Cybersecurity
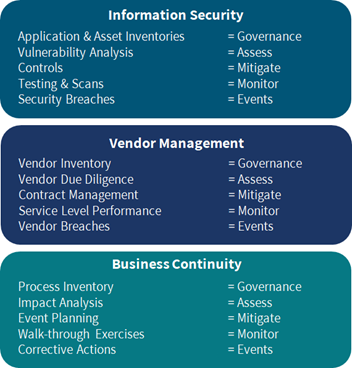
I call this tool a risk-based translation and recommend that auditors use this tool to understand the information given to them by different departments and have better communication with process owners about the insights they provide.
Get a Live Demo
If you’re interested in seeing LogicManager’s audit management software, request a personalized demo!
The Three Lines of Defense
To prevent cybersecurity issues, programs need to be created and implemented at every level of an organization. Traditionally, audit and risk professionals measure the effectiveness of existing programs by looking at the three lines of defense, as defined by The Institute of Internal Auditors (IIA).
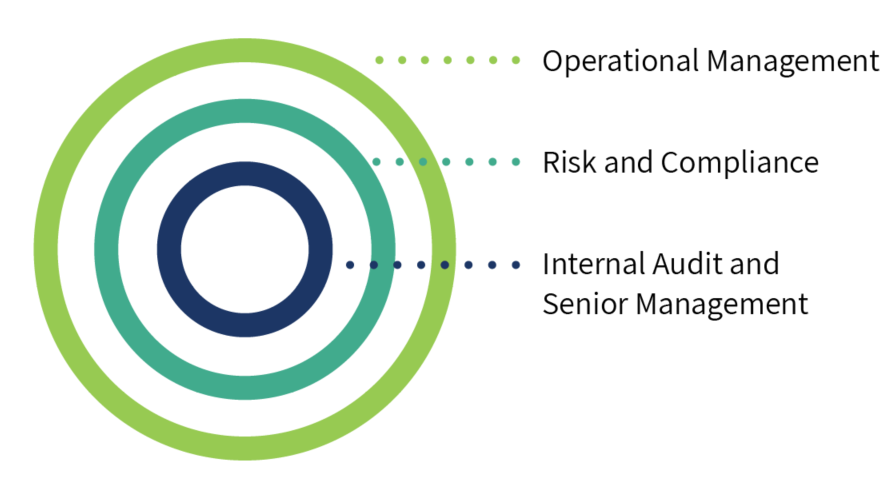
By using a common risk language across departments and with individuals in all three lines of defense, auditors can truly evaluate the effectiveness of cybersecurity programs and get an accurate picture of where their organization stands.
Risk transcends both departments and levels, so each of the three lines of defense should be involved:
- Operational Management: Front-line managers and process owners know the most about how risks and incidents materialize at an operational level. They can speak to how policies are operationalized, and where existing mitigation activities leave the company vulnerable on a day-to-day basis.
- Risk & Compliance: Risk and compliance professionals identify issues and can help enforce required controls. By partnering with risk and compliance, auditors can ensure they have a full understanding of what needs to be evaluated and when.
- Internal Audit Professionals and Management: Armed with all of this information, auditors can then test whether or not controls work, review associated metrics, and report their objective findings to senior management and the board of directors so it can be acted upon. When all information is collected with the same language and framework, auditors can detail their most important findings, so leadership teams can address critical issues and protect their organizations.
A risk-based process is the best approach to mobilize employees across all departments and silos; from front-line employees, to process owners, all the way to the board of directors.
Effective cybersecurity requires the right tone to be set from the top to empower the front-lines to identify risks and make them known.
Implementing a Risk-Based Approach
Implementing a risk-based approach and engaging your three lines of defense is a never-ending cycle. Too often, there is an overemphasis on the events; it’s essential to understand that a risk-based approach to cybersecurity does not end and continues with each audit.
Below is a tool that I find helpful in remembering the process. Use this wheel to pick an area to start within, and then use the risk translator to involve departments across your organization as you work through this iterative process.
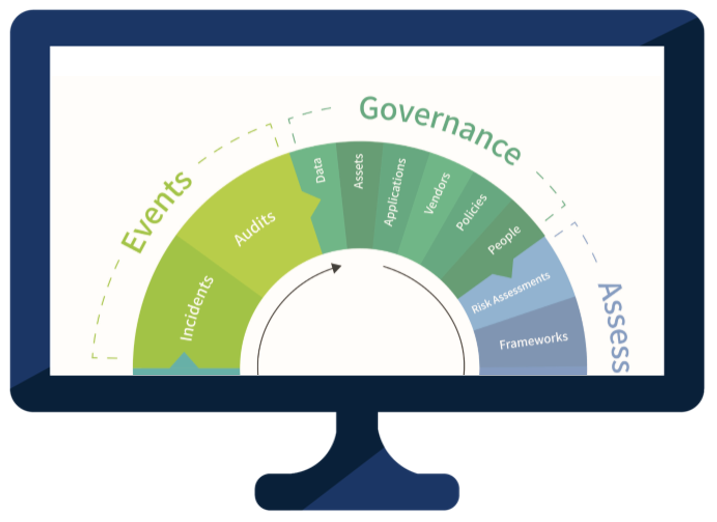
Download the Risk-Based Approach Wheel
Download the Risk-Based Approach Wheel to learn the order of operations enterprise risk management should follow.
With that framework in mind, all departments should apply the following process to cybersecurity in order to ensure that auditors’ findings are acted on by the right people, at the right time:
- Identify front-line risks that impact auditable entities. This includes readiness standards and frameworks such as ITGC, IIA recommendations, SANS, ISO, NIST, etc.
- Assess the impact and likelihood of these risks with a common framework and standardized assessment criteria. How do you objectively compare issues? Do controls align with best practice frameworks?
- Mitigate risks by mapping them and their controls to strategic goals.
- Monitor risks by determining the effectiveness of controls through testing (i.e. pen intrusion), incident management, metrics, and reporting. Which cyber risks were identified that are not addressed by any controls?
Everyone benefits from a risk-based approach.
A risk-based approach is beneficial because it allows cybersecurity risks to be aggregated across an organization and prioritized. This ensures the most critical risks are mitigated first, issues are identified, and resources are used efficiently.
For auditors, a risk-based approach is beneficial as it enables them to meet expectations set by the board of directors by identifying major tactical and strategic gaps in cybersecurity governance.
