Security Risk Management
IT Security Risk Management to Protect Your Reputation
LogicManager’s Security Risk Management solution empowers organizations to more effectively manage IT and Cybersecurity Risks and ensure compliance with regulations such as SOC 2, HIPAA, & ISO 27001, PCI DSS Compliance, NIST Cybersecurity Framework, COBIT, and more. Our IT Security & Governance solutions are fueled by a risk-based approach that allows customers to address risks in order of criticality. Adoption of this methodology will enable more efficient and thorough framework gap assessments, evidence collection, third party validation of completeness, issue and findings tracking, and reporting packages.
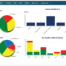
- Generate ready-made, configurable reports and dashboards to prove compliance to regulators and present to senior management.
- Centralize compliance information in a unified repository with a comprehensive risk library to simplify management and ensure adherence to standards and regulations.
- Conduct gap assessments against security frameworks and regulations like SOC 2, HIPAA, ISO 27001, and more
- Document controls and collect evidence to demonstrate their effectiveness.
- Conduct IT asset onboard & offboarding while ensuring proper access levels throughout your organization
- Identify IT Security issues and findings and track them to resolution.
For additional value:
Why Logicmanager? – Users of LogicManager’s ERM software explain how their ITRM programs have benefited from our platform and expert advisory service.
Customer Success StoriesExplore How Companies Overcame Challenges With Our Security Risk Management Solution
ERM Can Save Millions: Cybersecurity Case Study
A Santa Barbara-based non-profit organization suffered a breach of over 30,000 medical records caused by a third-party vendor that housed personal health information (PHI) without adequate security measures to safeguard the data, a disaster that could have been prevented with proper cybersecurity risk management.
What Our Customers Are Saying...
The LogicManager DifferenceA Holistic Approach to Security Risk Management

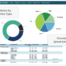
Business Decision InsightsFocus on What’s Important
Through our ERM software, we enable our customers to allocate more time to strategic risk management, reducing their involvement in tedious administrative activities like data cleansing and manipulation. Our solution enhances operational efficiency while uncovering the “unknown knowns” that risk managers may overlook, thus ensuring proactive identification and mitigation of risks.
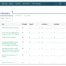
Customer ExperienceStreamline Your Risk Management Program
Unlike other software that requires IT professional customization, our solution allows customers to control engagement through an end-user configuration. This approach enables faster time-to-value and allows organizations to evolve their programs over time, not to mention a quicker return on investment.


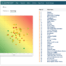
Risk-Based ApproachPrepare for Tomorrow’s Surprises Today
A risk-based approach is the key to effective governance, risk, and compliance. By adopting this methodology, organizations can prioritize their efforts across different departments, recognize potential hurdles and crucial interdependencies, and allocate resources appropriately. Embracing a risk-based mindset allows organizations to strategically allocate their resources to areas that hold the most value in terms of privacy protection and compliance.
Complimentary DownloadNIST Cybersecurity Framework Annotated Guide
Learn about the NIST Cybersecurity Framework, its key categories and subcategories, and how a risk-based approach can help your organization comply with this industry standard in our eBook, which also provides steps to identify, assess, mitigate, and monitor risk while partnering with an ERM system.
CapabilitiesAn All-In-One Security Risk Management Platform
Frequently Asked QuestionsFoundations of Security Risk Management
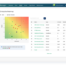
Security Risk Management software helps you identify and log critical assets, risks, and controls at each location to assess if they are protected with the right security measures that match the business’s risk appetites.
Cybersecurity risk management is the process of identifying an organization’s digital assets, reviewing existing security measures, and implementing solutions to either continue what works or mitigate security risks that may pose threats to a business.
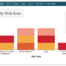
By taking a risk-based approach to cyber security risks, you will be able to prioritize risks in terms of importance and threat to the business to more effectively and efficiently manage risk.
Implementing a risk-based approach to cybersecurity risk management typically involves the following steps:
- Risk Identification: Identify and document potential threats, vulnerabilities, and risks specific to the organization’s information systems, assets, and operations. This can be done through risk assessments, security audits, and analysis of historical data.
- Risk Assessment: Evaluate the identified risks by assessing their likelihood of occurrence and potential impact. This involves considering factors such as the probability of a threat exploiting a vulnerability and the potential consequences of such an event.
- Risk Prioritization: Prioritize risks based on their potential impact and importance to the organization. This can be achieved by assigning risk levels or scores to each identified risk, taking into account factors such as the likelihood of occurrence and potential business impact.
- Risk Mitigation: Develop and implement risk mitigation strategies and controls to reduce the likelihood or impact of identified risks. This may involve implementing security measures, such as firewalls, encryption, access controls, employee training, and incident response plans.
- Monitoring and Review: Continuously monitor and review the effectiveness of the implemented risk mitigation measures. Regularly reassess risks to ensure that they are up to date and aligned with the evolving threat landscape and business priorities.
According to Gartner, IT risk management (ITRM) products are “software and services that operationalize the risk management life cycle of cyber and IT risks in the context of an organization’s mission. ITRM products are deployed to establish a central hub that facilitates business-related risk management.”
LogicManager uses the term See-Through Economy to explain the trend in fast-paced transparency, where consumers and investors are empowered to impact a company’s reputation. New technologies have left companies with nowhere to hide, meaning the See-Through Economy makes risk management more important than ever. With a mature ERM program, you can anticipate what’s ahead, uphold your reputation and protect your community.
Request a DemoLearn How LogicManager’s Security Risk Management Software Can Help Transform Your IT Governance and Cybersecurity Program
Speak with one of our risk specialists today and discover how you can empower your organization to uphold their reputation, anticipate what’s ahead, and improve business performance through strong governance.